6.4 Compare traditional campus device management with Cisco DNA Center enabled device management
Cisco DNA or Cisco Digital Network Architecture is Cisco’s software-defined architecture controller. Cisco DNA is managed from the Cisco DNA Center.
We should be careful not to use Cisco DNA Center with an operational legacy network because it might reconfigure existing equipment, which would cause disruptions.
We use Cisco DNA as a controller in a network that uses SDA or as a controller to manage a traditional network. We can install Cisco DNA and then gradually migrate our network. A Cisco DNA Center Appliance comes preinstalled with the Cisco DNA Center application.
We can connect to the Cisco DNA Controller via
- The Controller’s GUI
- A script that accesses the controller’s REST API
- A third-party app that accesses the controller via a REST API
- A script that accesses a third-party app via a REST API (which in turn accesses the controller via a REST API)
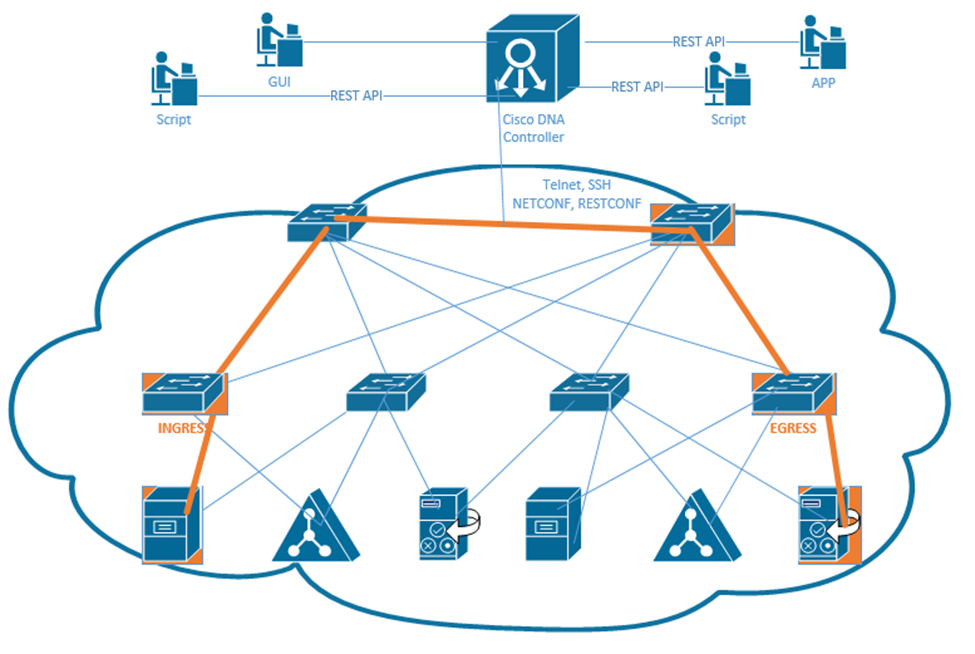
The Cisco DNA Controller has a Northbound REST API and many Southbound APIs. We use the northbound API and the GUI access the Controller and make changes to the network.
The southbound API can configure traditional devices over Telnet, SSH, or SNMP. It can configure newer devices via NETCONF and RESTCONF. More and more Cisco devices support NETCONF and RESTCONF.
On a traditional network, we can create ACLs to filter traffic. An ACL contains several rules, and the router applies each rule in order. As our network grows, we might add more and more rules. When there are dozens or hundreds of rules, it becomes difficult to edit or remove a single rule.
With Cisco DNA, we just create security policies. We define what types of devices can communicate, and what they’re allowed to communicate with. We don’t have to worry about their IP addresses. We don’t have to analyse the logic behind each ACL. Cisco DNA modifies the SDA fabric to reflect the policies we create. We can manage each policy separately without having to worry about how it affects other policies.
We can do this by creating users and groups. A user is a single individual. We can add a user to one or more groups. Each group is assigned specific policies. For example, the administrator group might have full access to the entire network. Users in the HR group have access to personnel records. Users in the engineering group have access to engineering documents.
Cisco calls these groups scalable groups and each group is assigned a scalable group tag, or SGT. We create a grid that specifies which groups can send traffic.
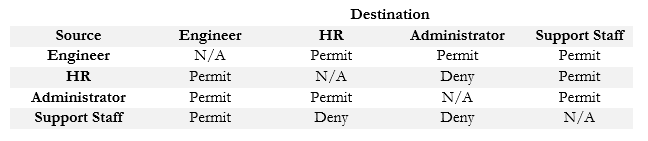
Now, when a device tries to send traffic, the ingress node first contacts the Cisco DNA Center. The Cisco DNA Center figures out which user is sending the traffic and what group he belongs to. Then it pulls up the appropriate policy. If the traffic is permitted, then the DNA Center tells the edge node that it can create a tunnel between itself and the destination edge node. If the traffic is not permitted, the DNA Center does not permit the tunnel to be created.
For example, if a member of the Support Staff group wants to send a message to a device in the Engineering group, it would be permitted. If a member of the Support Staff group wants to send a message to a device in the HR or Administrator group, it would be denied.
The benefit of using a group is that we are now basing security on the role of a user instead of the physical device connection. When devices can be shared by multiple users, providing security based on the physical device does not make sense.
The predecessor to Cisco DNA was Cisco Prime Infrastructure, or PI.
- PI allows us to manage all the network from a “single pane of glass”. That means we can manage the network from a single control panel instead of having to log in to each device separately.
- PI also manages the entire enterprise’s LAN, WAN, and device inventory.
- PI can determine a network’s entire topology. Cisco DNA can work with PI to obtain the data that PI discovered so that DNA does not have to rescan the network.
- Uses Telnet, SSH, CDP and LLDP to configure and manage traditional devices
- Allows us to install, configure and monitor devices
- Allows us to configure QoS
- Allows us to manage Wi-Fi and wired networks
- Maintains images of network operating systems through the Software Image Management or SWIM
- Allows plug and play configuration of new network devices. If we connect a new device, PI automatically configures it
PI is a software application that can be purchased and installed on your server or can be purchased as part of a separate physical appliance.
Cisco DNA supports SDA, whereas PI does not. But Cisco DNA is missing some of PI’s management features. Cisco DNA is still under development and will eventually contain all of the features included in PI. Some of Cisco DNA’s features
- EasyQoS allows us to manage Quality of Service through a graphical user interface
- Encrypted traffic analysis can detect malware inside encrypted traffic by looking for patterns and signatures
- Client health check allows us to view the health of any connected client. It provides a quality score from zero to ten. This feature might be known as Device360 or Client360.
- Network Time Travel allows us to go back in time and see how a client was performing. If we’re troubleshooting an issue, Network Time Travel allows us to return to the conditions that created the issue.
- Path Trace shows us the path a packet travels from the source to the destination. We can use this to detect latency and inefficient network layouts. It also shows us any ACLs that would interrupt the transmission.
